What a Phishing Attack Looks Like
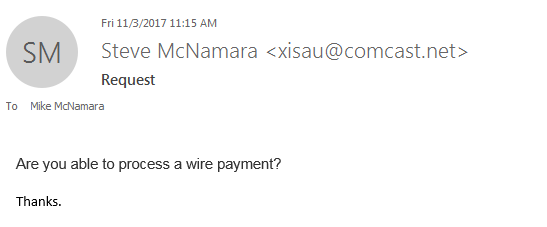
We were phished! Even an IT company can be vulnerable to phishing attacks. Mike McNamara, in Finance and Procurement, received the following email this morning:
A scammer took our CEO’s name and attempted to have Mike wire him some money. Thankfully, Mike was on alert right away about this odd and out-of-character request from “Steve.” Steve confirmed shortly that no, he did not email Mike regarding a wire transfer, and no, he does not have an obscure Comcast email address. Director of IT, Scott Leister, joined in to make sure the email didn’t transmit any malicious viruses or malware, and after it was determined that no damage was done, the whole office had a good laugh about the situation.
Don’t let yourself get caught up in a phishing attack! Even with spam filters in place, this email still found its way into Mike’s inbox. This is only one example of a phishing attack, and certainly not the most convincing one we have seen. Keep yourself, your business, and your money safe by following these tips:
Always think twice about clicking.
Most phishing attacks use malicious links to lure you into providing the scammers with sensitive account information. If the email looks odd, don’t click. Even if the email doesn’t look odd, don’t click it – some scam emails can look very realistic. A common phishing attack method is asking to renew account information or update payment information. If you get an email from ‘Netflix’ asking for updates to your account, go directly to their site instead of clicking through the email. If it really is Netflix and they really do need new information, it will notify you on their legitimate website as well.
Check the source.
In Mike’s case, simply looking at the sender’s email showed that the request for a wire payment was a scam. If the sender’s email seems odd, don’t trust it. However, attackers are getting sneakier about getting harmful emails into your inbox. Hacked accounts – from your friends, your bank, or other companies – can look like perfectly legitimate emails. Or, emails will have just a few characters out of place. For example, example@netflix.com looks very similar to example@netf1ix.com, depending on fonts used. There is no foolproof way to identify and filter scam emails. Human intuition is the best way to prevent phishing scams.
Have a backup plan in place.
Even the most secure networks can be affected by phishing attacks. You can do everything possible to protect your network, but there’s always the chance that an email will slip through your security borders. Backing up your data, using multi-factor authentication on accounts, monitoring your accounts for threats, and keeping passwords secure are just a few ways to build a backup plan in case you find yourself breached by an attacker.